What do data diodes and "Zone 30" have in common?
What is a data diode?
A data diode, also sometimes called one-way or unidirectional technology, is a powerful security measure. Just as with a diode – the electronical component where current can only flow in one direction (from anode to cathode) – a data diode allows data to flow in one direction only. Nowadays, there are lots of scenarios where data from your OT environment needs to flow to other parts: on-premise IT systems, cloud systems, … However you want to make sure that a cyber security issue within IT cannot impact your factory.
A data diode can be very helpful here.
Where a firewall is something logical (a ruleset one needs to program, allowing for errors or bugs), a data diode is something physical. The comparison with a diode is not coincidental: in a data diode it is physically not possible to have data flowing in the opposite direction.
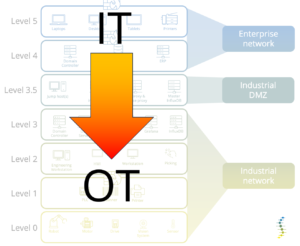
If you would have such one-way device as the sole communication path between your OT zone and your IT zone, there is no way a cyber attack from IT can reach OT directly from the IT zone.
Why isn't it used more?
But if such data diode is that powerful, why is it not being used almost everywhere on the OT security perimeter?
Unfortunately, the benefits it brings in most cases do not outweigh the limitations. Again it has something to do with human behaviour.
Picture the situation where you drive in a so-called “Zone 30” (a zone, typically around schools or in crowded city centers) where the maximum speed limit is 30km/h.

In the morning, when school starts and a lot of kids are on the go, it is easier to understand why you drive in a zone 30.
We all know that we would dramatically reduce traffic fatalities if everyone drove at a maximum speed of 30km/h.
But a lot of people decide that the benefit of reduced driving time and the ability to go farther are worth the increased risk of driving much faster than 30km/h. We have added seatbelts, airbags, and we have our driving skill to reduce the risk to a level which – individually – we accept.
It’s basically the same with our OT security perimeters. Companies accept the added risk of allowing network traffic from IT into the OT zone even though they know it increases the likelihood of compromise!
They choose to implement advanced firewalls, perimeter monitoring and other controls (think of the forementioned seatbelts, the airbags, …) to reduce, but not eliminate the added likelihood of compromise.
The business cases and benefits of 2-way communication between OT and other networks are increasing, and this means the locations where one-way data diodes makes sense, will be reduced.
Ask yourself the following questions
Ask yourself the following questions, when thinking about IEC 62443 Foundational Requirement 5 – Restricted Data Flow (RDF):
- do I have to send data in 2 directions? Or is only 1 direction sufficient?
- if it is only in 1 direction: why would I deploy a firewall? Why am I accepting this unnecessary increase in risk?
- how did I decide that 2-way communication is needed? Only by capturing existing communication and turning it into a firewall ruleset?
- are all the existing 2-way communications worth the additional risk?
Spinae OT security specialists are here to help
Our OT security specialists can help you to think about Restricted Data Flow, about the network architecture, about traffic flows, … Feel free to contact us to get our expert view on the matter!

